 That Nigerian prince requesting bank account information may be easy email fraud to spot, but what if a spoofed email arrived looking exactly like your boss? Business Email Compromise (BEC) scams are misleading employees into diverting company payments to swindlers who are impersonating customers, vendors, or senior executives.
That Nigerian prince requesting bank account information may be easy email fraud to spot, but what if a spoofed email arrived looking exactly like your boss? Business Email Compromise (BEC) scams are misleading employees into diverting company payments to swindlers who are impersonating customers, vendors, or senior executives.
According to FBI statistics, $1.6 Billion was lost by US companies between October 2013 and December 2016. Common scenarios cited by the FBI include fraudulent correspondence through a compromised email from a vendor or client, attorney impersonation, and wire transfer requests from a spoofed or hacked CFO email address.
The Hanover Insurance Group created a piece “Stop Imposter Fraud scams before they happen”. It's an excellent read pertaining to BEC. I’ve condensed some of their ideas from seven to four tips.
1) Verify all changes to fund transfer payments over the phone.
Employees with the authority to transfer funds should not change vendor, client, or employee bank account information without first confirming the change with a phone call. This phone number must be previously established and not a number provided on a potentially fraudulent email.
2) Be suspicious of emails calling for a rush transfer.
An email crafted to pressure an employee into transferring funds hastily should be a red flag. Employees should be trained not to fall victim to intimidation that might cause them skip authentication procedures.
3) Limit the number of employees with wire transfer authority.
Fewer authorized personnel mean fewer targets for fraudsters. Supervisors should be required to sign off on changes to vendor or client/customer bank account information or internal/external wire transfers.
4) If a scam email has been detected consult IT.
Stop the bleeding lest others be scammed. If a fraudulent email is coming from someone internally, your network likely has been breached. Actions should to be taken to secure the companies network.
Most insurance policies will not cover a BEC scam. The willful parting of money is often excluded from the language of contracts and usually requires the insured to add false pretense coverage to an existing plan.
Prevention is the ideal solution to BEC scams. Once compromised though, your only lifeline is false pretense coverage which normally is an addition. Be sure you’ve talked to your agent about the proper Social Engineering coverage.

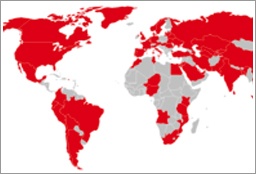 Over the last week the WannaCry ransomware was released and spread to over 200,000 computers in over 100 countries throughout the world. Following WannaCry, a new attack called Adylkuzz has crippled computers over 150,000 computers. Both attacks exploit a vulnerability in the Microsoft operating systems that are no longer being supported, even though Microsoft did release a patch in March to protect against an attack. Also this week, a hacking group called Shadow Brokers posted an internet message saying it would release a new trove of cyber-attack tools next month.
Over the last week the WannaCry ransomware was released and spread to over 200,000 computers in over 100 countries throughout the world. Following WannaCry, a new attack called Adylkuzz has crippled computers over 150,000 computers. Both attacks exploit a vulnerability in the Microsoft operating systems that are no longer being supported, even though Microsoft did release a patch in March to protect against an attack. Also this week, a hacking group called Shadow Brokers posted an internet message saying it would release a new trove of cyber-attack tools next month.
 he growing network of internet connected devices are continuously changing the way we live and work. Nowadays it is not surprising to find computing devices embedded in everyday objects, enabling them to send and receive data via the internet.
he growing network of internet connected devices are continuously changing the way we live and work. Nowadays it is not surprising to find computing devices embedded in everyday objects, enabling them to send and receive data via the internet. ith another year in the books, we took a look back at the top 5 most popular R&R articles of last year.
ith another year in the books, we took a look back at the top 5 most popular R&R articles of last year.